Not so long ago, seeing how my (and every) computer was basically opened to the four winds when connected to anything, i decided to explore a new way to regain some control on what happens on my network.
When connecting a computer to the internet, it'll look for updates and send telemetry reports without even telling you. If you're infected by a malware, it may silently connect to others peers and start distributing harmful content without even you knowing.
Even if some common OS built-in firewalls allow a per-apps access filtering, once you start browsing the web, you would got ads you didn't wanted with your content, and your computer will be connected to tracking domains as well.
Basically, the problem is that you don't really have a choice of what your computer is connecting to, because the web is open.
There are solutions around but they aren't perfect, so built my own tool and have been used it ever since. Here is a system-wide, efficient and radical solution that solve many problems at once.
The first thing to know is that everything that reach your computer has been explicitely requested by it, and it often start with sending DNS requests. At this point, good security is more about filtering what's going out rather what's coming in, and filtering outgoing DNS is a good way to start.
That's what tools like Pi-Hole are doing, but it can be easily circumvented if your gateway doesn't filter DNS requests addressed to another DNS server.
Another popular approach is to use DNS blocklists, but this approach is imperfect, as these lists needs to be continuously maintained, and will always lag behind emergence of new threats. Plus, several hundreds of thousands of blocking rules may become gradually unsustainable for low-power hardware, and these rules can be just ignored by the OS itself.
On top of that, none of these solutions work against hard-coded destination adresses. It won't prevent a bad actor to communicate with a server configured with a fixed IP address (8.8.8.8 is a well known google DNS server. Big vendors can afford to maintain these servers afloat for a long time)
The best way to regain control of your network would be to just block every outgoing traffic and gradually allow what you want, but it will require a lot of effort allowing remote hosts, and maintain those rules as destination IP are changing over time.
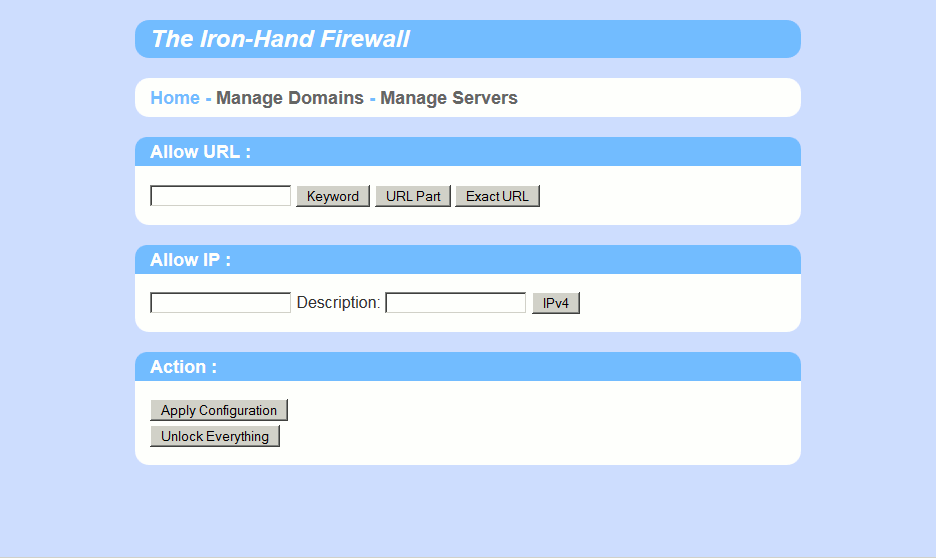
The system is installed on a dedicated device on the network which act as a gateway and a DNS server. It blocks everything by default, drop DNS requests not addressed to him, and resolve to a false address every DNS requests that don't match a domain list. When a DNS requests is allowed, the response is parsed to allow access to the associated remote host. There is a second list of allowed IP addresses for convenience, and that's all.
Let's see what it mean:

Pictured device is an Orange Pi R1, hosting the firewall. It can also be used as a VPN gateway. By being managed by a separate device, it ensure there won't be any leak.
If the VPN connection drop for any reason, the gateway won't be automatically switched to the default connection, thus preventing any packet transmission through an unencrypted connection.
The interface is pretty clear. Multiple URL can be added at once. There is color on the URL list to quickly see what is a keyword matching rule (less secure) or an exact URL matching rule (more secure).
It can still be improved but it works.
I haven't stopped using it since then. Knowing how you're unreachable give a great safety feeling. Adding URLs to the list was a bit painful at first but i don't even think about it. Some websites appears very broken but as long as i have access to content, i don't really care. Overengineered design is what is killing the web.
The only unplanned surprise is that i'm having more than 3000 entries on the list right now. I thought, like probably many users, that i "just go on a dozen of website on a regular basis". In fact, it's a bit more than that.
The hardest part in using this everyday is figuring which domains are needed by a specific website. It require monitoring of DNS requests and findind out which are needed, and a community-driven database of "good" subdomains would be a top project to launch and maintain.
I still have some work to do, but i'll release it somedays.